Which of the Following Best Describes a Susceptible Host
Epidemics occur when an agent and susceptible hosts are present in adequate numbers and the agent can be effectively conveyed from a source to the susceptible hosts. For each of the following risk factors and health outcomes identify whether they are necessary causes sufficient causes or component causes.

Break The Chain Of Infection Infectionpreventionandyou Org
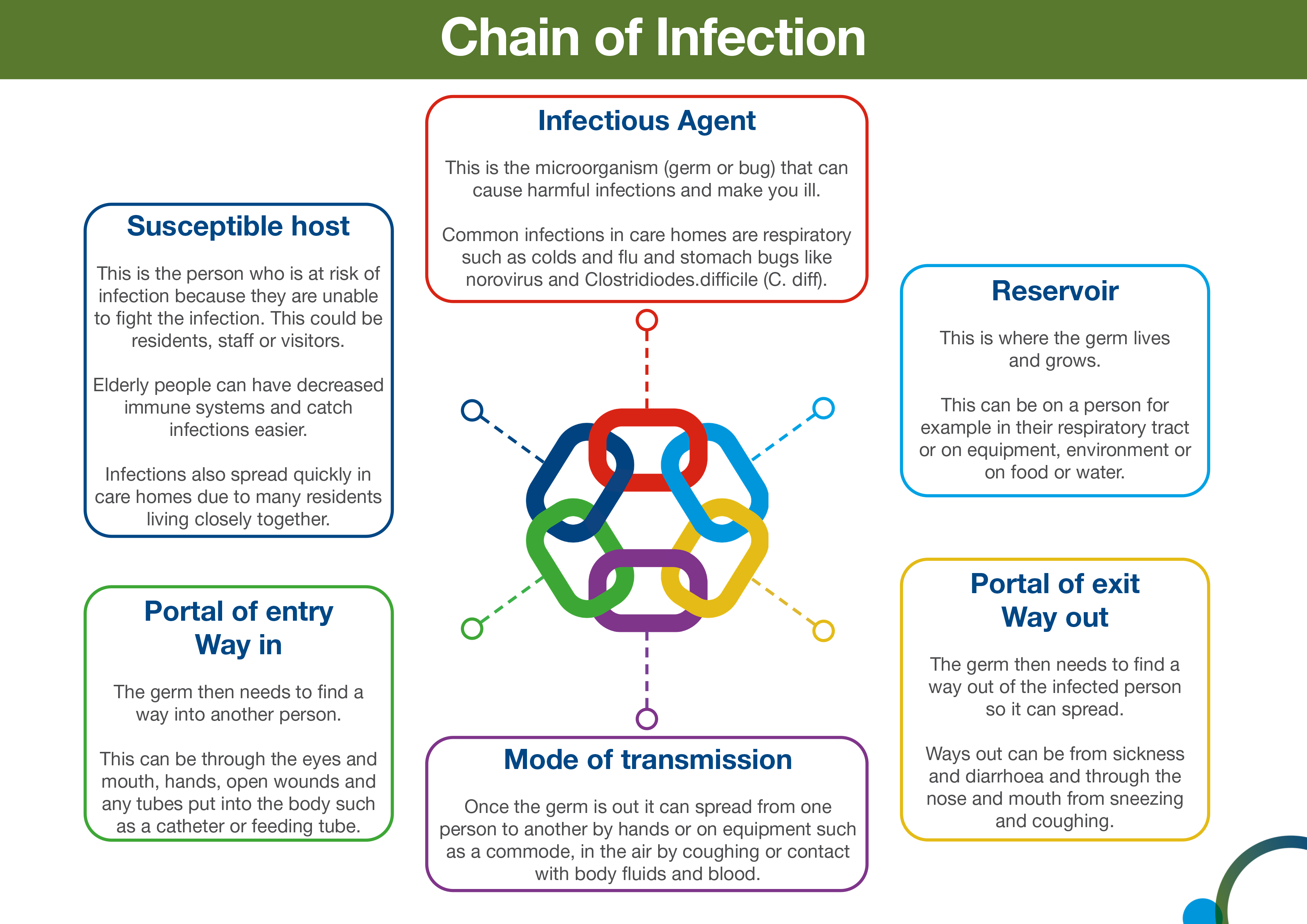
It states that microorganisms known as pathogens or germs can lead to disease.
. January 29 2022 by Sagar Aryal. A penicilloyl polylysine skin test yields positive results. Joe an employee receives an email stating he won the lottery.
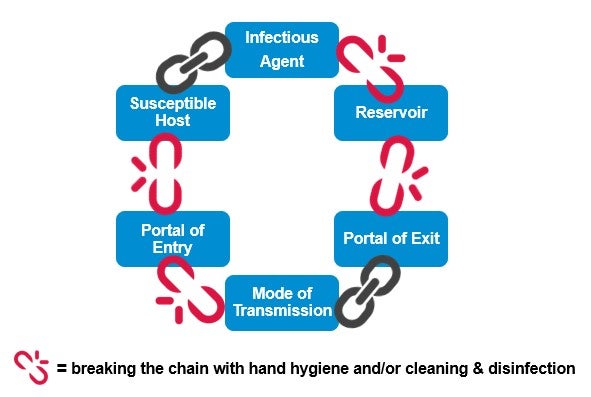
LESS susceptible to ping and SYN floods but MORE susceptible to IP spoofing. SUSCEPTIBLE PERSON HOST A susceptible or non-immune person is one who has little resistance against a particular organism and who if exposed to this organism is likely to contract disease. 1 Susceptible host 2 Portal of exit 3 Infectious agent 4 Reservoir host 5 Means of transmission 6 Portal at entry a 123456 b 234561 c 342561 d 432651.
A recent increase in amount or virulence of the agent The recent introduction of the agent into a setting where it has not been before. Read the Anthrax Fact Sheet on the following 2 pages then answer the questions below. Which of the following best describes session hacking.
Previous antibiotic treatment resulted in severe rash fever and systemic anaphylaxis almost immediately. Which of the following best describes the order of occurrence of the infection cycle. Whether there is any presence of malnutrition or dehydration.
And are a portal of exit. Which of the following BEST describes this type of email. Which of the following best describes the order of occurance if the links in the chain of infection.
Which of the following best describes session hacking. The email includes a link that requests a name mobile phone number address and date of birth be provided to confirm Joes identity before sending him the prize. PORTAL OF ENTRY The opening where an infectious disease enters the hosts body such as mucus membranes open.
MA 10110 Final Study Guide 1. However the germ theory of disease has many limitations. The last link in the chain of infection is the susceptible host.
Malicious hacker Answer 1. By contrast an immune person is one who has a high degree of resistance to the organism and who when exposed does not develop the disease. A description of the susceptible host.
A 13-year-old male with cystic fibrosis develops repeated episodes of pneumonia resulting in multiple hospitalizations. 1 susceptible host 2 portal of exit 3 infectious agent 4 reservoir host 5 means of transmission 6 portal of entry A 123456 B 234561 C 342561 D 432651. Typhus Lyme disease and Rocky Mountain spotted fever are from the family.
Why might a proxy gateway be susceptible to a flood attack. The and the are the best type of susceptible host. More specifically an epidemic may result from.
Add your answer and earn points. Which of the following statements best describes a white-hat hacker. Which of the following best describes the order of occurrence of the infection cycle.
A white-hat hacker is a good guy who uses his skills for defensive purposes. Whether there is any underlying chronic disease. Source mode of transmission susceptible host John Snow Robert Koch Kenneth Rothman For each of the following identify the appropriate letter from the time line in Figure 127 representing the natural history of disease.
Which is a firewall vendor manufacturing a host-based firewall for Windows 2000 Server Sun Solaris and Red Hat Linux environments. Describe its causation in terms of agent host and environment. The method by which a pathogen is transmitted.
Former grey hat D. The way a pathogen is treated once it enters the body. Which of the following best illustrates the type of hypersensitivity reaction.
Myrandaduro2005 is waiting for your help. A process for killing pathogens. How susceptible any host will be depends on a variety of factors.
Which of the following is an advantage of the network host based configuration. Former black hat C. It allows multiple simultaneous connections.
Epidemiologic Triad- Agent Host Environment. Their age and in particular if they are very young or very old. Direct contact between infectious host and susceptible host or indirect transmission which involves an intermediate carrier like an environmental surface or piece of medical equipment.
A security audit performed on the internal network. The germ theory of disease is the currently accepted scientific theory for many diseases.
Introduction To Ipc Infection Prevention And Control
Covid 19 The Chain Of Infection Transition From Hospital To Home Cloroxpro
Belum ada Komentar untuk "Which of the Following Best Describes a Susceptible Host"
Posting Komentar